Information Security Officer Resume Examples and Templates
This page provides you with Information Security Officer resume samples to use to create your own resume with our easy-to-use resume builder. Below you'll find our how-to section that will guide you through each section of a Information Security Officer resume.


What do Hiring Managers look for in an Information Security Officer Resume
- Cybersecurity Expertise: In-depth knowledge of cybersecurity principles, best practices, and the ability to assess and mitigate security risks.
- Compliance and Regulations: Proficiency in understanding and ensuring compliance with relevant data security laws and industry regulations.
- Risk Management: Capability to identify and manage security risks, conduct risk assessments, and develop security strategies.
- Incident Response: Experience in developing and implementing incident response plans and effectively handling security incidents.
- Communication Skills: Effective communication and interpersonal skills to educate employees on security best practices, liaise with external stakeholders, and report on security initiatives.
How to Write an Information Security Officer Resume?
To write a professional Information Security Officer resume, follow these steps:
- Select the right Information Security Officer resume template.
- Write a professional summary at the top explaining your Information Security Officer’s experience and achievements.
- Follow the STAR method while writing your Information Security Officer resume’s work experience. Show what you were responsible for and what you achieved as an Information Security Officer.
- List your top Information Security Officer skills in a separate skills section.
Advance your cybersecurity career with a professionally tailored resume. Our cybersecurity resume writing service highlights your technical expertise, threat mitigation skills, and security leadership to help you stand out in a competitive job market.
How to Write Your Information Security Officer Resume Header?
Write the perfect Information Security Officer resume header by:
- Adding your full name at the top of the header.
- Add a photo to your resume if you are applying for jobs outside of the US. For applying to jobs within the US, avoid adding photo to your resume header.
- Add your current Information Security position to the header to show relevance.
- Add your current city, your phone number and a professional email address.
- Finally, add a link to your portfolio to the Information Security Officer resume header. If there’s no portfolio link to add, consider adding a link to your LinkedIn profile instead.
Bad Information Security Officer Resume Example - Header Section
Daniel 167 Hamilton Drive Phillipsburg, NJ 08865 Marital Status: Married, email: cooldude2022@gmail.com
Good Information Security Officer Resume Example - Header Section
Daniel Gilbert, Phillipsburg, NJ, Phone number: +1-555-555-5555, Link: linkedin/in/johndoe
Make sure to add a professional looking email address while writing your resume header. Let’s assume your name is John Doe - here is a formula you can use to create email addresses:
- firstnamelastname@email.com - johndoe@email.com
- firstname.lastname@email.com - john.doe@email.com
- lastname.firstname@email.com - doe.john@email.com
- f.lastname@email.com - j.doe@email.com
- l.firstname@email.com - d.john@email.com
- firstnamelastname12@email.com - johndoe12@email.com
For a Information Security Officer email, we recommend you either go with a custom domain name (john@johndoe.com) or select a very reputed email provider (Gmail or Outlook).
How to Write a Professional Information Security Officer Resume Summary?
Use this template to write the best Information Security Officer resume summary: Information Security Officer with [number of years] experience of [top 2-3 skills]. Achieved [top achievement]. Expert at [X], [Y] and [Z].
How to Write an Information Security Officer Resume Experience Section?
Here’s how you can write a job winning Information Security Officer resume experience section:
- Write your Information Security Officer work experience in a reverse chronological order.
- Use bullets instead of paragraphs to explain your Information Security Officer work experience.
- While describing your work experience focus on highlighting what you did and the impact you made (you can use numbers to describe your success as a Information Security Officer).
- Use action verbs in your bullet points.
Information Security Officer Resume Example
Information Security Officer
- Introduced the Information Security Officer role within the AMNX group.
- Formulated an information security strategy and established an information security governance framework.
- Delivered routine reports on information security.
- Designed and oversaw an effective information security training program.
- Implemented an information security management framework aligned with ISO27001 and ITIL standards.
- Managed the information security function by continuously addressing incidents and risks.
- Collaborated in the development of AMNX's IT Security product portfolio.
Chief Information Security Officer Resume Example
Chief Information Security Officer
- Developed and executed management policies and strategies to enhance information security.
- Enforced IT security standards for the advancement of the Bank's information system.
- Applied standards and guidelines for classifying information assets and data ownership.
- Conducted employee awareness campaigns on IT security.
- Reported to the bank's board of directors, regulatory agencies, and shareholders on all IT security-related matters.
Information Security Officer Resume Example
Information Security Officer
- Conducted Penetration Testing and vulnerability assessments on clients' networks, systems, and data centers.
- Created and implemented Vulnerability and Patch Management frameworks for clients.
- Developed Information Security Incident Management Frameworks.
- Designed Information Security Policy Frameworks for clients, following ISO 27001 standards and customized to specific client requirements.
- Established an annual Information Security Awareness Program.
- Conducted Security Assessments and analysis of client infrastructure.
- Managed and maintained security operations for Libyaroots' public website.
Information Security Officer Resume Example
Information Security Officer
- Monitored the corporate-wide network devices to identify vulnerabilities and applied patches for enhanced security using Manage Engine Desktop Central.
- Ensured proper functioning and updated status of the Agent on all corporate-wide network devices, resolving any operational issues.
- Addressed threats targeting corporate-wide network devices.
- Verified the installation and functionality of Data Loss Prevention (DLP) and USB Block on all corporate-wide network devices.
- Monitored inbound and outbound threats within the Office 365 mail system, taking measures to block them and prevent further threats.
- Regularly checked the CPU, disk, and memory health of corporate-wide servers using OpsManager to ensure continuous operation.
- Conducted Information Security Awareness programs to educate corporate-wide employees about Information Security.
- Established department-specific Shared Folders, assigned appropriate members access privileges, and managed website accessibility.
- Played a role in Information Security decision-making, including policies and procedures, and ensured their implementation and compliance.
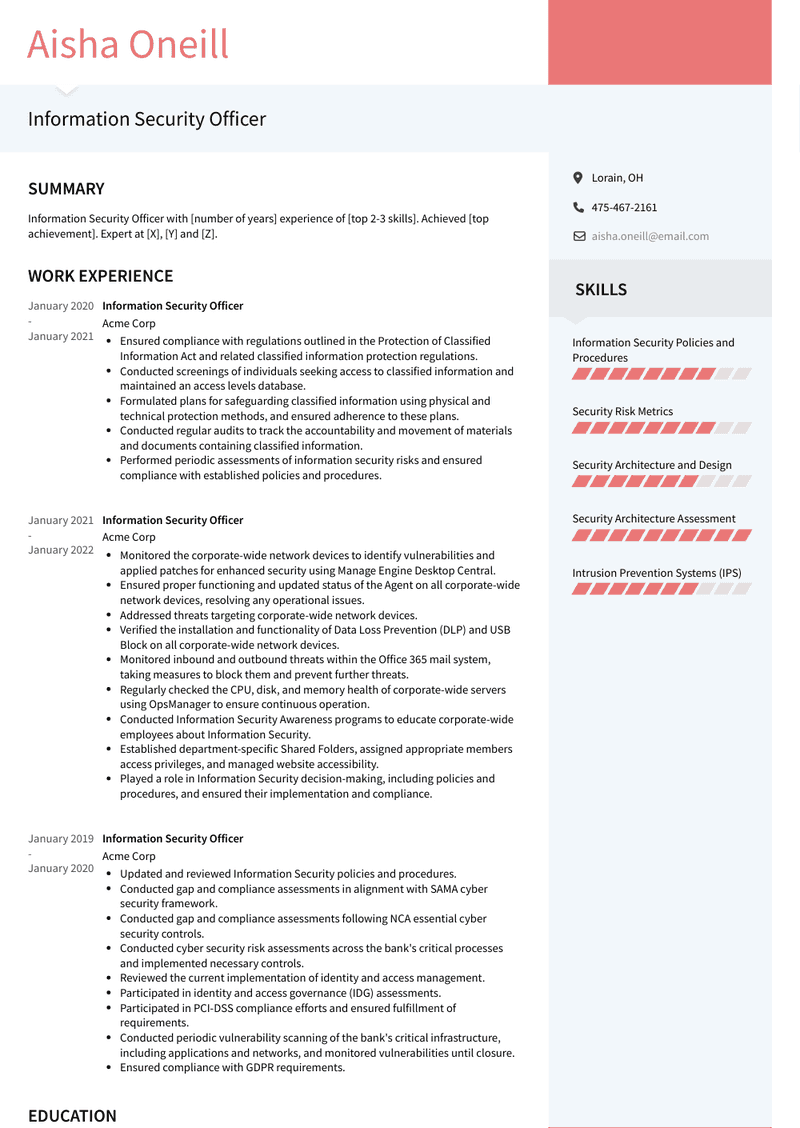
Information Security Officer Resume Example
Information Security Officer
- Ensured compliance with regulations outlined in the Protection of Classified Information Act and related classified information protection regulations.
- Conducted screenings of individuals seeking access to classified information and maintained an access levels database.
- Formulated plans for safeguarding classified information using physical and technical protection methods, and ensured adherence to these plans.
- Conducted regular audits to track the accountability and movement of materials and documents containing classified information.
- Performed periodic assessments of information security risks and ensured compliance with established policies and procedures.
Information Security Officer Resume Example
Information Security Officer
- Updated and reviewed Information Security policies and procedures.
- Conducted gap and compliance assessments in alignment with SAMA cyber security framework.
- Conducted gap and compliance assessments following NCA essential cyber security controls.
- Conducted cyber security risk assessments across the bank's critical processes and implemented necessary controls.
- Reviewed the current implementation of identity and access management.
- Participated in identity and access governance (IDG) assessments.
- Participated in PCI-DSS compliance efforts and ensured fulfillment of requirements.
- Conducted periodic vulnerability scanning of the bank's critical infrastructure, including applications and networks, and monitored vulnerabilities until closure.
- Ensured compliance with GDPR requirements.
IT Information Security Officer Resume Example
IT Information Security Officer
- Led global IT strategy across 10 corporate locations, developing and implementing an IT Roadmap to address business challenges effectively, cost-efficiently, and in the best interests of Bazaarvoice.
- Provided career development and guidance to a dedicated, skilled IT team. Collaborated with Bazaarvoice senior leaders to enhance operations and technology in support of business objectives.
- Constantly assessed IT services to reduce software redundancy and legacy infrastructure. Established a metrics-based SLA model to gauge IT performance. Optimized SFDC, finance, and HR sys admin efforts through governance and aligning with company priorities.
Top Information Security Officer Resume Skills for 2023
- Information Security Policies and Procedures
- Risk Assessment and Management
- Security Frameworks (e.g., NIST, ISO 27001)
- Threat Detection and Analysis
- Incident Response Planning
- Security Auditing and Compliance
- Security Awareness Training
- Vulnerability Assessment
- Penetration Testing
- Security Incident Investigation
- Security Architecture and Design
- Network Security
- Endpoint Security
- Firewall Configuration and Management
- Intrusion Detection Systems (IDS)
- Intrusion Prevention Systems (IPS)
- Security Information and Event Management (SIEM)
- Access Control
- Identity and Access Management (IAM)
- Data Encryption and Decryption
- Public Key Infrastructure (PKI)
- Security Patch Management
- Security Risk Metrics
- Security Incident Reporting
- Security Governance
- Security Awareness Campaigns
- Security Compliance Audits
- Cloud Security
- Mobile Device Management (MDM)
- Security Policies Enforcement
- Regulatory Compliance (e.g., GDPR, HIPAA)
- Security Awareness Programs
- Security Threat Modeling
- Security Awareness Metrics
- Social Engineering Awareness
- Security Documentation and Standards
- Business Continuity Planning (BCP)
- Disaster Recovery Planning (DRP)
- Security Education and Training
- Secure Software Development Practices
- Incident Response Plan Testing
- Security Policy Development
- Security Risk Assessment Tools
- Security Incident Management
- Secure Coding Practices
- Secure Network Design
- Security Architecture Assessment
- Security Strategy Development
- Security Technology Evaluation
- Continuing Education in Information Security
How Long Should my Information Security Officer Resume be?
Your Information Security Officer resume length should be less than one or two pages maximum. Unless you have more than 25 years of experience, any resume that’s more than two pages would appear to be too long and risk getting rejected.
On an average, for Information Security Officer, we see most resumes have a length of 2. And, that’s why we advise you to keep the resume length appropriate to not get rejected.
How can I highlight my experience as an Information Security Officer on my resume?
Focus on your expertise in developing and implementing security policies, managing risk assessments, and ensuring compliance with security standards. Highlight your role in safeguarding organizational data, responding to security incidents, and leading security awareness initiatives.
What are the key skills to feature on an Information Security Officer's resume?
Emphasize skills in cybersecurity, risk management, and regulatory compliance. Detail your experience with security frameworks like ISO 27001, NIST, or GDPR, as well as your expertise in incident response, encryption, and vulnerability management.
How do I demonstrate my ability to manage security policies on my resume?
Provide examples of how you’ve created, enforced, or enhanced security policies to mitigate risks. Mention any successful implementations of security strategies that protected critical systems and data.
Should I include metrics on my Information Security Officer resume? If so, what kind?
Yes, include metrics such as reductions in security incidents, the number of successful audits, or cost savings from risk mitigation. These figures help quantify your impact and demonstrate your ability to strengthen security.
How can I showcase my experience with regulatory compliance on my resume?
Detail your role in ensuring compliance with industry standards and laws like GDPR, PCI-DSS, or HIPAA. Highlight your involvement in audits, risk assessments, and maintaining regulatory documentation.
What kind of achievements should I highlight as an Information Security Officer?
Highlight achievements such as reducing vulnerabilities, successfully managing security breaches, or leading significant security upgrades. Mention any awards or recognition received for excellence in cybersecurity management.
How do I address a lack of experience in a specific area of information security on my resume?
Emphasize your core information security skills and your ability to learn and adapt. Highlight relevant training, certifications, or projects that demonstrate your capability in managing security issues effectively.
How important is incident response for an Information Security Officer role?
Incident response is critical for an Information Security Officer, as it ensures swift action during security breaches. Highlight your experience with incident response protocols, including detection, containment, and recovery processes.
How do I demonstrate my ability to manage cybersecurity teams on my resume?
Mention your leadership experience, including how you’ve managed security teams, assigned responsibilities, and ensured team alignment with security goals and policies.
Should I include certifications on my Information Security Officer resume?
Yes, include certifications such as Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), or Certified Ethical Hacker (CEH). These demonstrate your knowledge and commitment to maintaining high cybersecurity standards.
-
What do Hiring Managers look for in an Information Security Officer Resume
-
How to Write Your Information Security Officer Resume Header?
-
How to Write a Professional Information Security Officer Resume Summary?
-
How to Write an Information Security Officer Resume Experience Section?
-
How can I highlight my experience as an Information Security Officer on my resume?
-
What are the key skills to feature on an Information Security Officer's resume?
-
How do I demonstrate my ability to manage security policies on my resume?
-
Should I include metrics on my Information Security Officer resume? If so, what kind?
-
How can I showcase my experience with regulatory compliance on my resume?
-
What kind of achievements should I highlight as an Information Security Officer?
-
How do I address a lack of experience in a specific area of information security on my resume?
-
How important is incident response for an Information Security Officer role?
-
How do I demonstrate my ability to manage cybersecurity teams on my resume?
-
Should I include certifications on my Information Security Officer resume?
Copyright ©2025 Workstory Inc.